Articles
Latest Articles

CISA Warns Federal Agencies About Windows Kernel Vulnerability
CISA, the Cybersecurity and Infrastructure Security Agency, is currently alerting federal agencies about "ongoing attacks" targeting a high-severity Windows kernel vulnerability. That vulnerability is tracked as CVE-2024-35250, an untrusted pointer dereference weakness which enables hackers to gain system privileges. The...
December 17, 2024

Cyberattack May Have Compromised Personal Data of “Hundreds of Thousands” of Rhode Islanders
Cyberattacks are always serious, but some affect user privacy more than others. So it is with this case in Rhode Island, which leaves the data of hundreds of thousands of residents exposed. On December 5, Deloitte noticed a breach of...
December 17, 2024

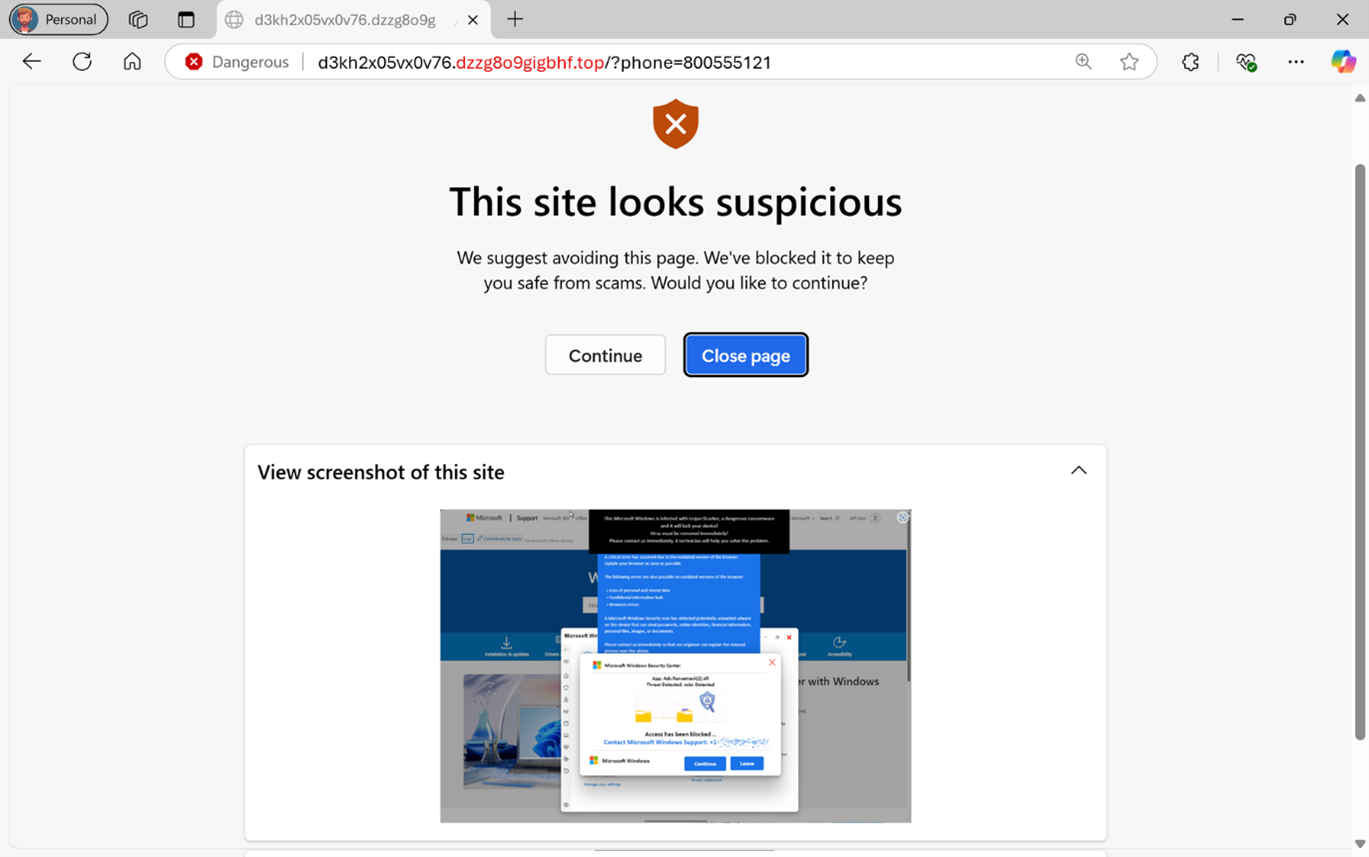
Don’t Be Fooled by This Subtle Scammer Trick
Scammers rely on a serious of tactics that, unfortunately for them, are no longer so subtle. Many of the classic signs of spam and scam are both well known and easy to spot, which is how so many messages end...
December 10, 2024

Attackers Target Major Health Device Manufacturer
Bad actors have recently turned their sights on Artivion, a heart surgery medical device manufacturer. The company disclosed they were the subject of a ransomware attack that occurred on November 21, and the attack was severe enough to both affect...
December 10, 2024

Microsoft’s Free Wallpapers App Isn’t Private
Microsoft recently introduced "Bing Wallpaper" to the Microsoft Store. This free app offers up a new wallpaper each day, featuring an image taken from around the world. It seems like an easy download: Fresh, interesting, daily wallpapers, all free of...
December 2, 2024

Microsoft Fixes Four Security Flaws
Microsoft has found and fixed four security flaws that span across four of its various products. One of these flaws affects Copilot Studio, Microsoft's program for customizing its AI. In addition, one of these flaws has an active exploit in...
December 2, 2024
Microsoft 365 Services Affected by Outage
If you had some issues with Microsoft 365 services on Monday, you weren't alone. Microsoft was working to fix an outage affecting many of its 365 services, including Exchange Online, Microsoft Teams, and SharePoint Online. Impacted users had also reported interruptions...
November 26, 2024

Watch Out for These Holiday Scams
You might not associate the holidays with scams, but it is prime season for certain bad actors. Unfortunately, there are numerous potential targets this time of year, as scammers see gifts being bought and exchanged in record volume. To keep yourself...
November 26, 2024

Hannaford’s Website and Mobile App Are Back Online Following “Cybersecurity Issue”
Last week, we covered how Ahold Delhaize USA, parent company to grocery store chains Hannaford and Stop & Shop, was the target of a cyberattack. As such, the company took some systems offline, and ran into supply issues at certain...
November 19, 2024

How to Use LinkedIn’s New “Open to Volunteering” Feature
If you log into LinkedIn, you'll probably see profiles with an "Open to Work" badge, denoting users who are actively looking for recruitment. However, this "Open to" feature has other options as well, including "Open to Volunteering." This feature could...
November 18, 2024