Articles
Latest Articles

Vietnamese Government Agents Attempted to Infect U.S. Congressmen’s iPhones
We all need to be on the lookout for hacking, but some of us need to be more careful than others. The higher profile you are, the more likely you are to be targeted in one of these attacks. That’s...
October 10, 2023

The NSA Is Creating an Artificial Intelligence Security Center
As AI—specifically generative AI—continues to capture the attention and imagination of us all, it becomes more evident than ever that we need to be prepared to live in an AI-influence world. Governments, as it seems, are well aware of this...
October 3, 2023

Thinking About AI’s Role in Election Security
One of the biggest stories in cybersecurity over the last decade or so has been election interference. The internet empowers hackers in different countries to meddle in other nations’ election processes. But there’s a new factor we haven’t seen in...
October 3, 2023

Watch Out for PDF Phishing Schemes
Scams are an unavoidable part of daily life these days. But that doesn't mean all scams are the same: There is a huge variety of ways hackers and bad actors attempt to steal your personal information, with no end in...
September 26, 2023
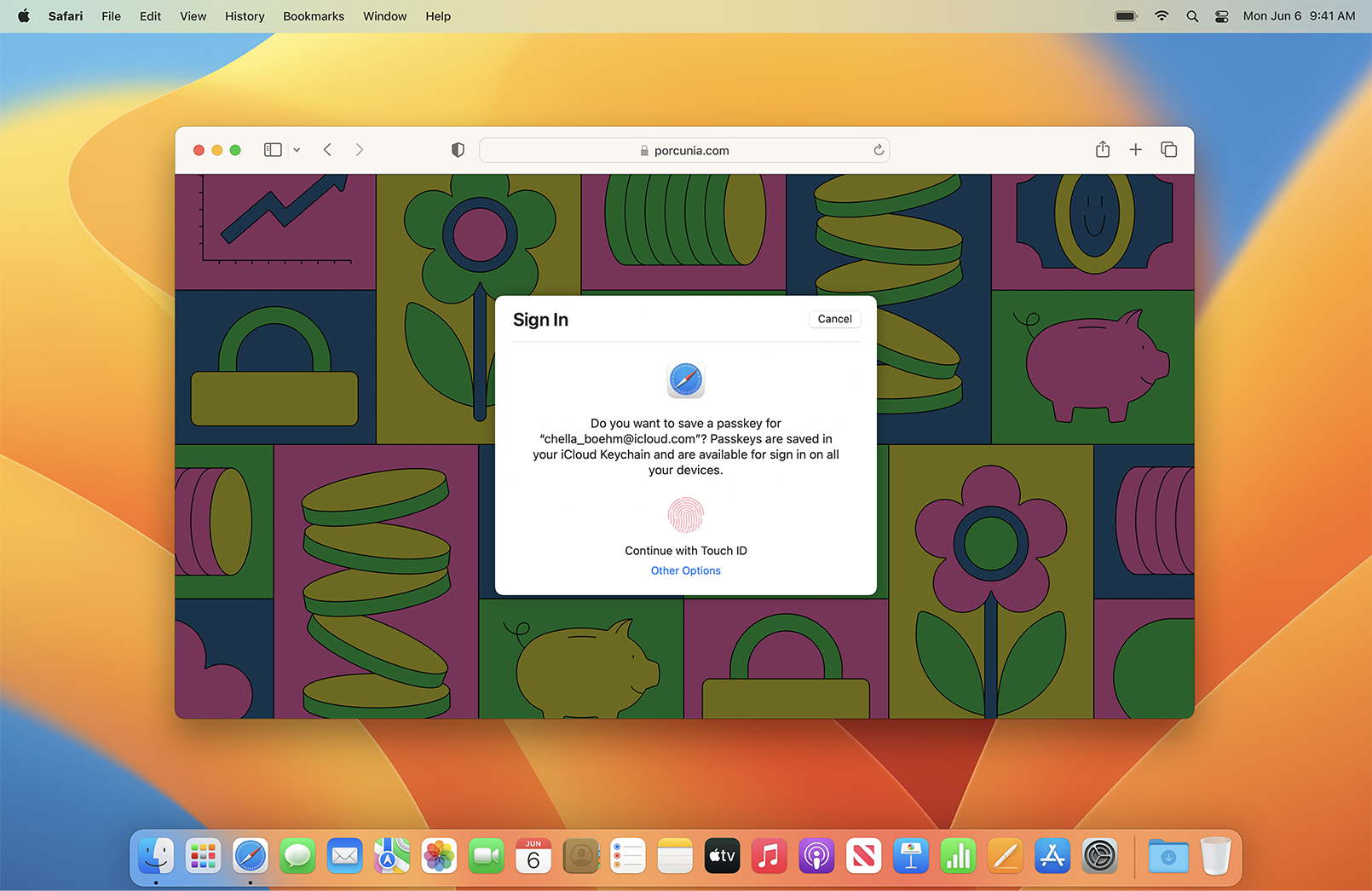
Passkeys Are Here to Replace Passwords
We all have a lot of passwords. Ideally, each one is strong and unique, but that isn't always the case. Many of us reuse the same, weak passwords, which leaves our digital data vulnerable to hacking. Even if our passwords...
September 26, 2023

Apple’s ‘Lockdown Mode’ Can Protect Against the Worst Cyberattacks
We all have to deal with cybersecurity threats. Calls, texts, and emails from scammers and bad actors can jeopardize our data and digital lives. However, a small percentage of us have cybersecurity issues that are far more serious. Journalists, politicians,...
September 19, 2023

Scammers Are Getting Better at Stealing Money From You and Your Business
While many still fall for even the most basic of scams these days, more of us than ever are educated on what to look out for. You probably know, for example, that a call about your "car's extended warranty" is...
September 19, 2023

MGM Shuts Down Computers Across the Country Due to Cybersecurity Issue
No business is immune to cybersecurity threats—not even casinos. A "cybersecurity issue" has caused MGM Resorts International to shut down computers across some of its casinos and hotels here in the US. This issue reportedly started Sunday, affecting properties in...
September 12, 2023

What Apple’s Latest Software Update Means for Your Security
Apple's latest security update is one you won't want to skip. Whether you have a personal Apple device or one for work, a new security flaw is currently threatening both your private and business data. The company released its newest...
September 12, 2023
Watch Out for Charity Scammers
Phone scams are becoming more and more sophisticated. While they can be easy to spot—such as a call about your car's extended warranty—they can also be clever, and trick you into thinking there's a legitimate caller on the other end...
September 5, 2023