Articles
Latest Articles

The US and UK Accuse China of Spying on Millions of Citizens
Officials from the US and UK accused the Chinese government of an extensive cyberespionage scheme that targeted millions of people, ranging from lawmakers, academic, journalists, and companies. Both countries filed charged and imposed sanctions on Beijing in retaliation. The list...
March 26, 2024
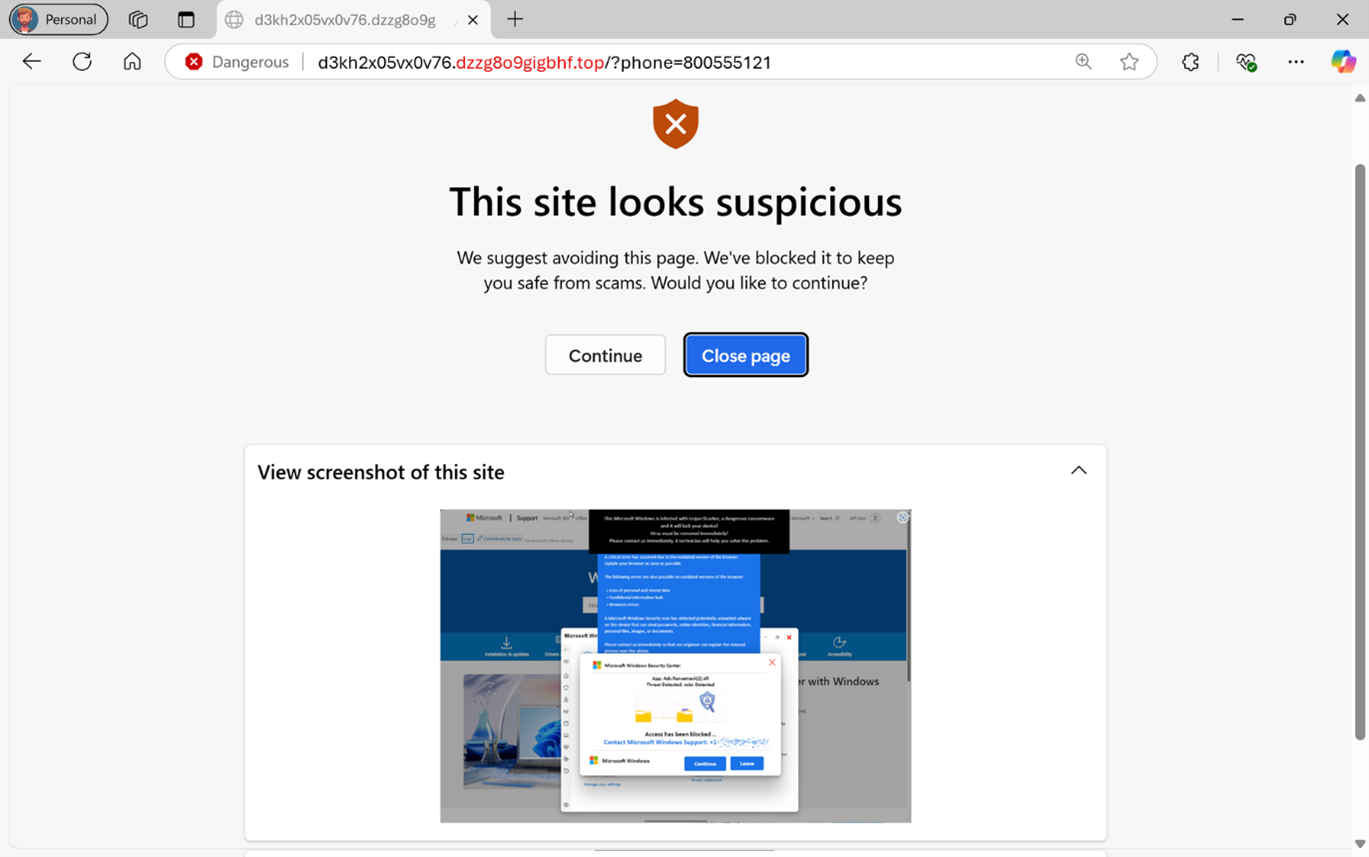
How SEO Poisoning Can Threaten Your Business
When you want to look something up on the internet, you turn to a search engine, like Google or Bing. However, not all links are relevant, or even legitimate. Bad actors are devising ways to trick you into clicking on...
March 26, 2024
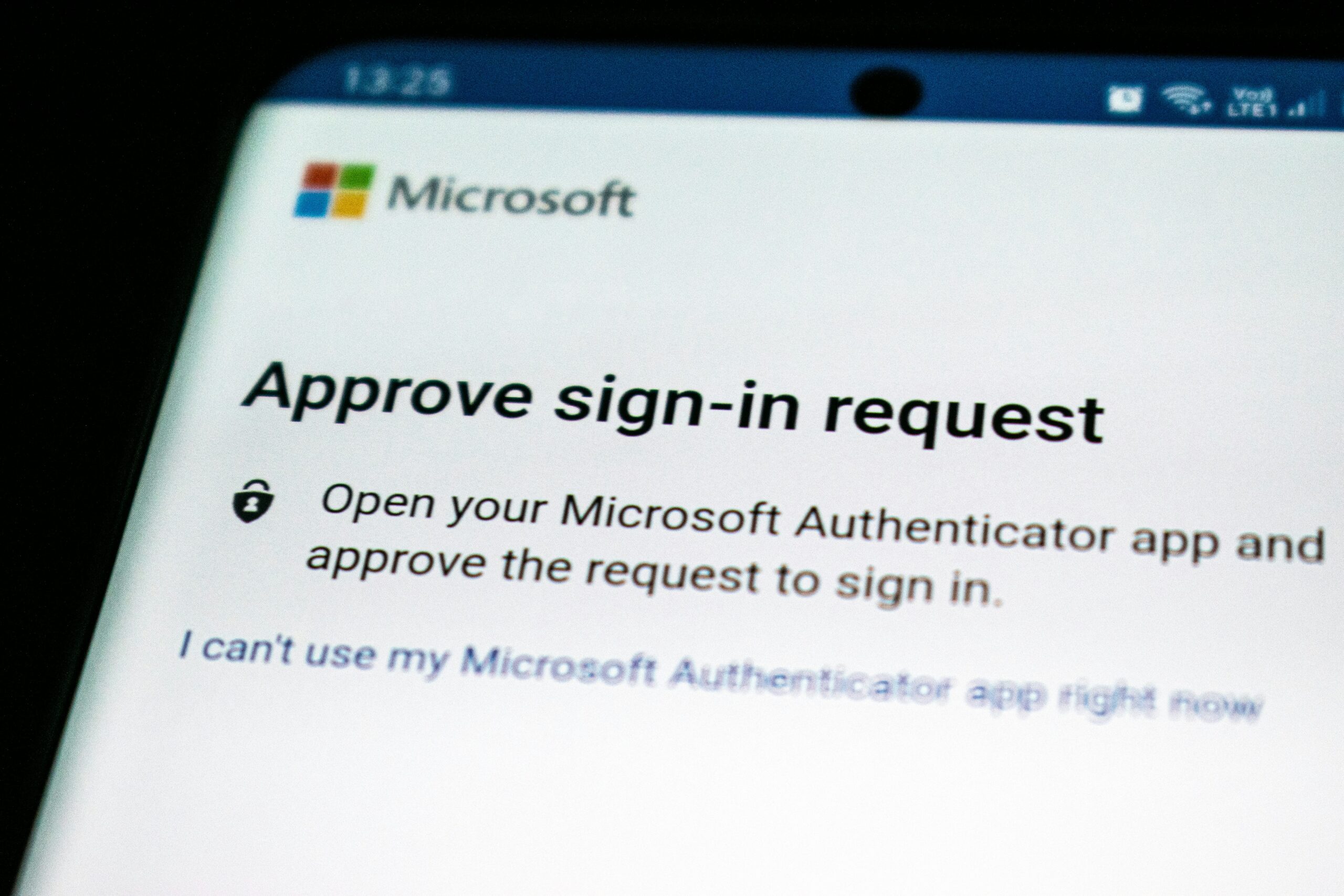
Unprompted MFA Codes Are Bad News
Multi-factor authentication (MFA) is one of the most powerful tools in your cybersecurity arsenal. When enabled, MFA can prevent bad actors from breaking into your accounts, even when they have your username and password in hand. Because MFA is so...
March 19, 2024
Is ChatGPT a Security Threat?
ChatGPT took the world by storm, and for good reason: The generative AI chatbot is capable of many feats, and continues to improve as more and more people test out how artificial intelligence can improve their productivity. However, new research...
March 18, 2024

Microsoft Has a Russian Hacker Problem
You read that right: Microsoft can't seem to shake its Russian hackers. The company said Friday it was still attempting to remove the "elite" Russian government hackers that breached the email accounts of senior executives back in November. Worse yet,...
March 12, 2024

US DoJ Arrests Former Google Engineer for AI Tech Theft
As reported by The Hacker News, the US Department of Justice (DoJ) has indicted a Chinese national and resident of California. The 38-year-old's charge? Allegedly stealing AI trade secrets from Google while secretly employed at two different Chinese-based tech companies....
March 12, 2024

What to Do When Your Wi-Fi Seems Slow
When the internet is working as it should, you think nothing of it. Clicking on a website takes you where you want to go instantly, and sitting down for a video call is seamless. But when your Wi-Fi starts slowing...
March 5, 2024

The FBI Is Watching Out for AI Attacks in the Upcoming Election
The FBI expects the 2024 election to be a target for cyberattacks, especially those generated by artificial intelligence, FBI Director Christopher Wray told a national security conference. Specifically, Wray called these threats "fast-moving," in the face of technology that could...
March 5, 2024

Protect Your Accounts from SIM-Swap and Port-Out Attacks
There isn't one type of cyberattack out there, nor is there one point of entry for hackers to target. While attacks commonly occur through computers and internet accounts, your smartphone is an increasingly popular target. In fact, hackers can completely...
February 27, 2024

What Happens When Windows Server OS Reaches End of Life?
No matter what type of technology you're using, it's important to stay up to date with the latest updates and security patches. That applies to servers, as well: If your business is using an outdated version of Windows Server OS,...
February 25, 2024